I participate as SKR in Battle of 1337 last weekend, and it was quite fun! Here are the challenge writeups
Challenges
Simplify
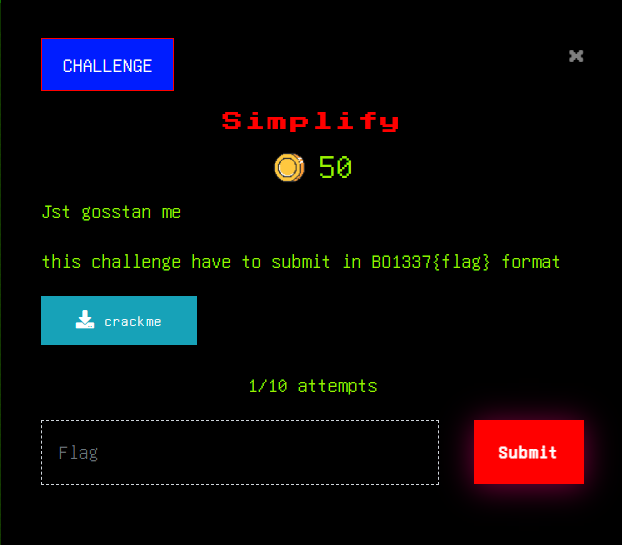
Attachment
Download the file, it is a ELF file means is a linux executable file
crackme: ELF 64-bit LSB shared object, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=f75eeac944f72065eacfdcc28ebfdcba4d02d639, for GNU/Linux 3.2.0, not stripped
Try to run it, it ask to enter a code:
./crackme
Enter code: asdf
Wrong code..
Let’s try to open it with Ghidra!
Decompiled main function:
undefined8 main(undefined8 param_1,undefined8 param_2)
{
undefined8 in_R9;
long in_FS_OFFSET;
int local_20;
uint local_1c;
uint local_18;
uint local_14;
long local_10;
local_10 = *(long *)(in_FS_OFFSET + 0x28);
printf("Enter code: ");
__isoc99_scanf("%i-%i-%i-%i",&local_20,&local_1c,&local_18,&local_14,in_R9,param_2);
if ((((local_20 + local_14 * 3 == 0x467c) && (local_1c * local_18 * 3 == 0x4ef3ae)) &&
(local_20 == 0x3f2)) && (local_18 * 0xc0d3 + local_14 == 0x3cbbd6c)) {
printf("Correct code! The flag is %i-%i-%i-%i\n",0x3f2,(ulong)local_1c,(ulong)local_18,
(ulong)local_14);
}
else {
puts("Wrong code..");
}
if (local_10 != *(long *)(in_FS_OFFSET + 0x28)) {
/* WARNING: Subroutine does not return */
__stack_chk_fail();
}
return 0;
}
As you can see, we need to enter 4 numbers in format of 1-2-3-4 and it will check if is the correct code
If correct means the code is the flag!
Math
Do some math to calculate the correct code, assume the code is a-b-c-d, we need to satisfy all 4 condition where:
a= 0x3f2a+3d= 0x467cc x 0xc0d3 + d= 0x3cbbd6c3bc= 0x4ef3ae
By using substitution method we can solve all unknowns:
a = 1010
3d = 17034, d = 5678
c x 49363 + 5678 = 63683948, c = 1290
3b x 1290 = 5174190, b = 1337
So the correct code is 1010-1337-1290-5678
Verify with the program:
./crackme
Enter code: 1010-1337-1290-5678
Correct code! The flag is 1010-1337-1290-5678
Therefore the flag is:
BO1337{1010-1337-1290-5678}
Back To The Future
We are given a link https://b2f.battleof1337.com/
Go to the link given, seems like a static website
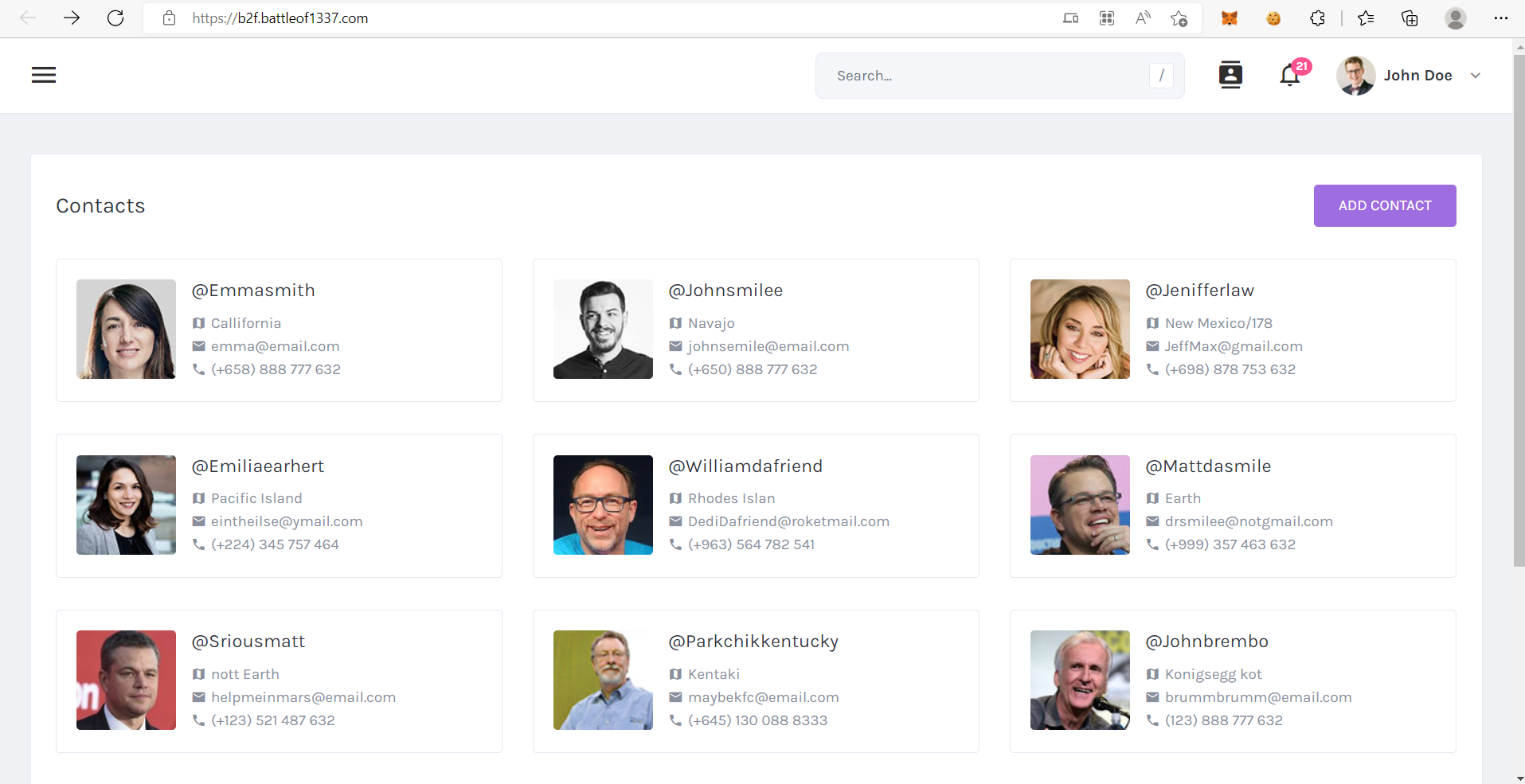
The challenge description says:
Delorean if only we can see back our pass is it great?
So I guess we need to use wayback machine in archive.org so we can see the previous version of the website
After searching the URL given, saw got a snapshot on 4th July!
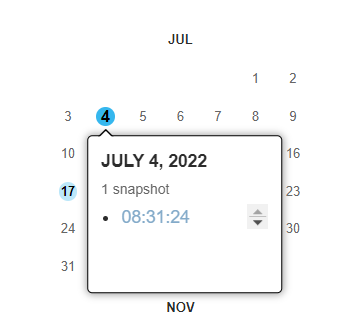
Click the link, wait awhile and saw the flag!
Flag
BO1337{aHR0cHM6Ly9veW0uY2F0bWUuY2Y=}
Break the storage
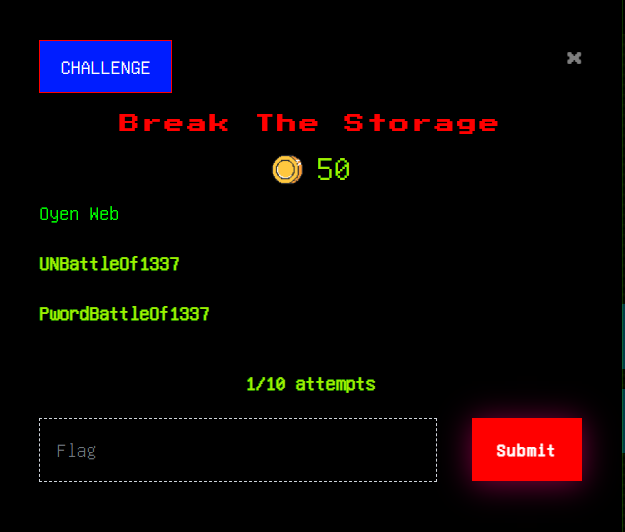
We are given a link https://oyen.battleof1337.com/login.html
Go to the link given, saw login page with username and password:
Tried the credentials in the challenge description, it login successfully and redirect to https://oyen.battleof1337.com/profile.html
Inspect the page, and saw profile.js
let database = "data";
$.get(database, function(a) {
jsons = JSON.parse(a),
getFlag = jsons.user.super,
window.localStorage.userID == getFlag.userID && alert("BO1337{a2c13e70ff50376e259ddb5bd5e54a69b16e569f}"),
0 == window.localStorage.length && (window.location = "login.html")
});
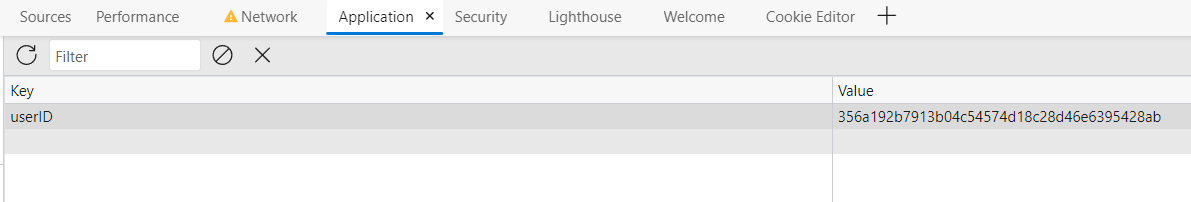
Seems like we need to set local storage to the super userID, which is 356a192b7913b04c54574d18c28d46e6395428ab (check from https://oyen.battleof1337.com/data), then it will show a popup flag
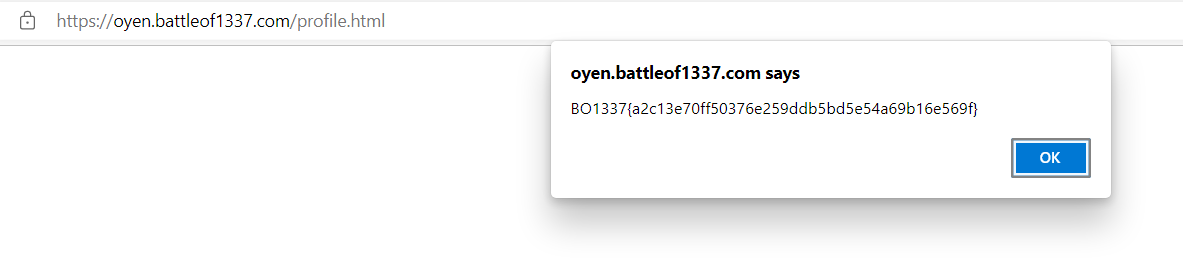
Flag
BO1337{a2c13e70ff50376e259ddb5bd5e54a69b16e569f}
Cat-Dalmantion
We are given a link http://ifelse.battleof1337.com/
Click the link, just a website with 2 buttons, showing black or white cat
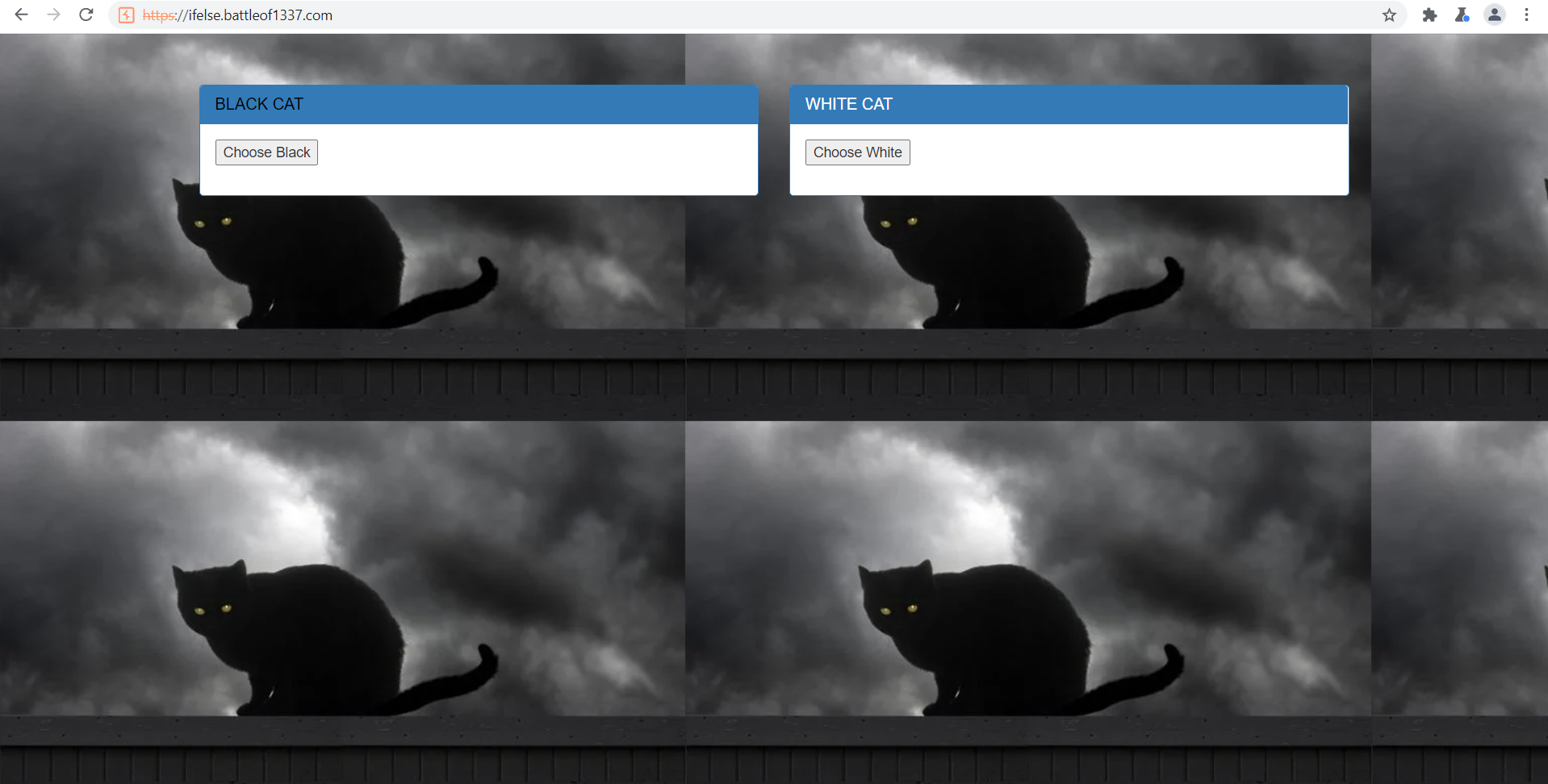
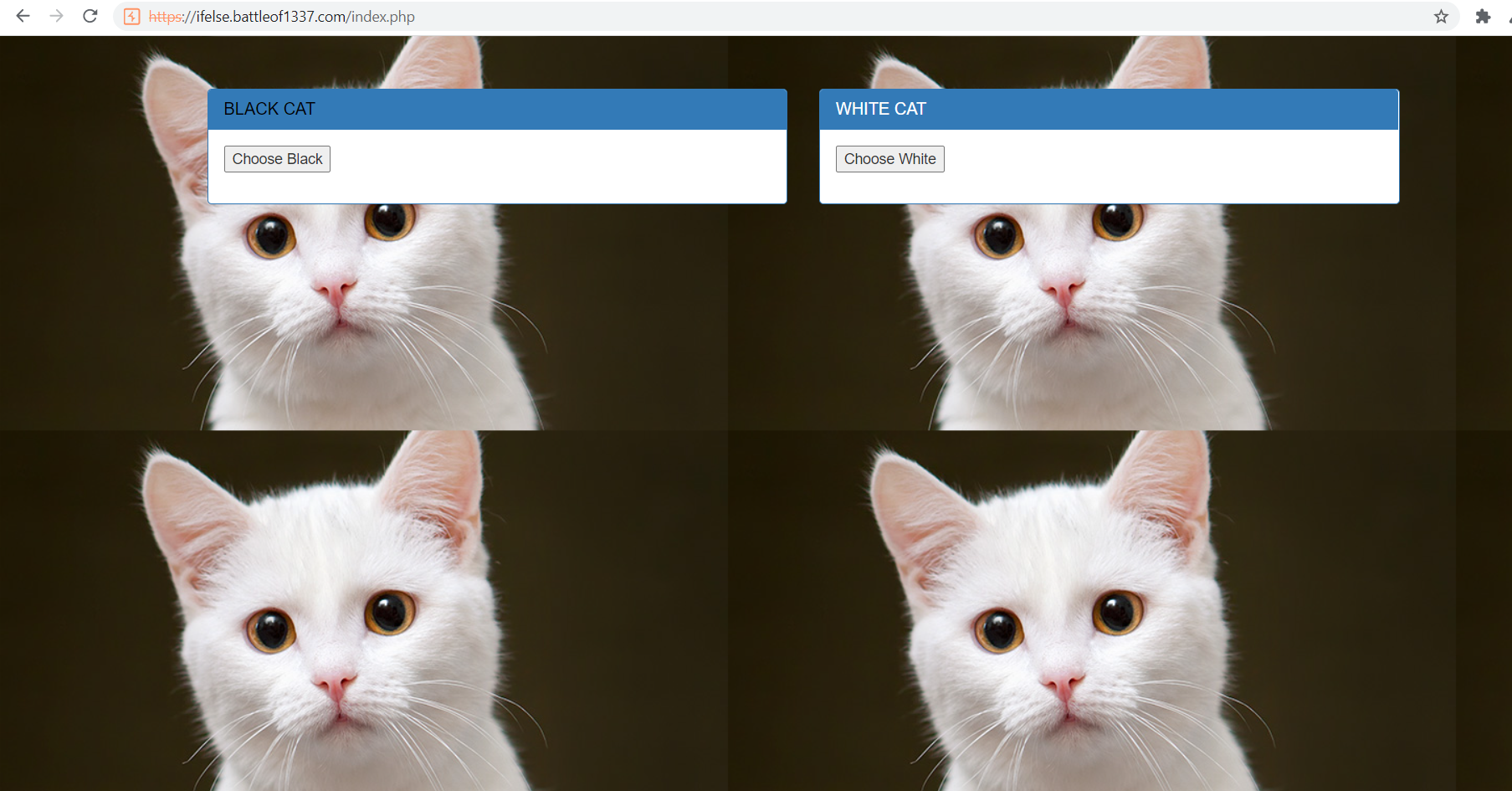
Check the request on burpsuite, it show white cat when send POST request and show black cat when send GET request
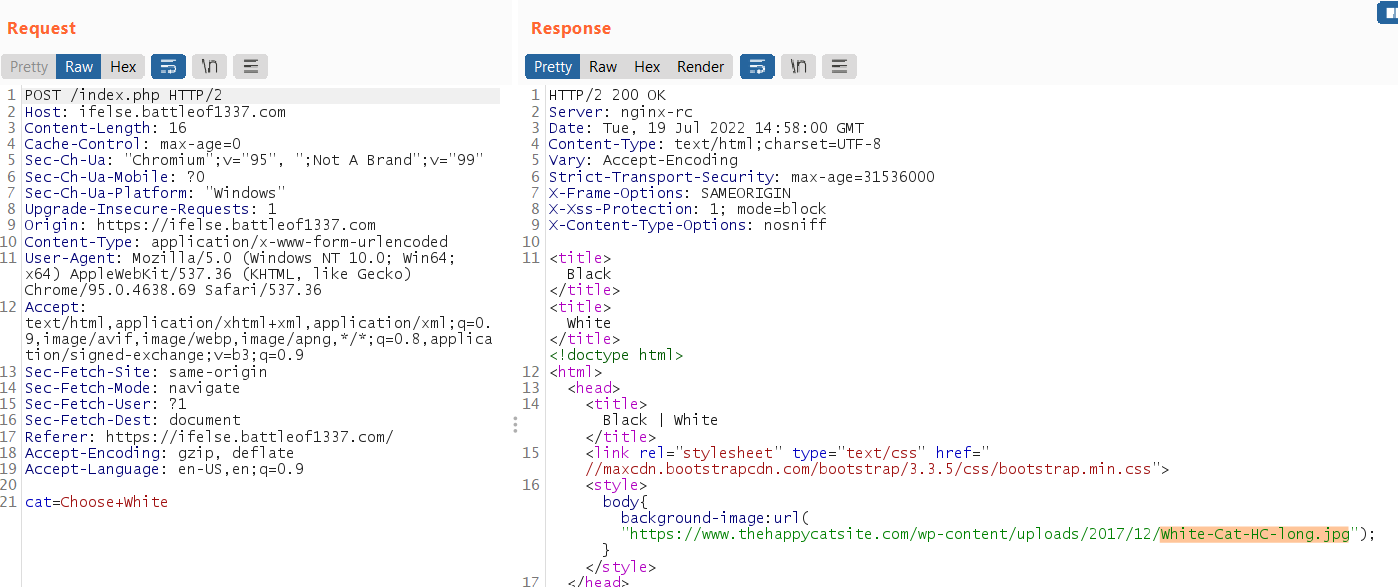
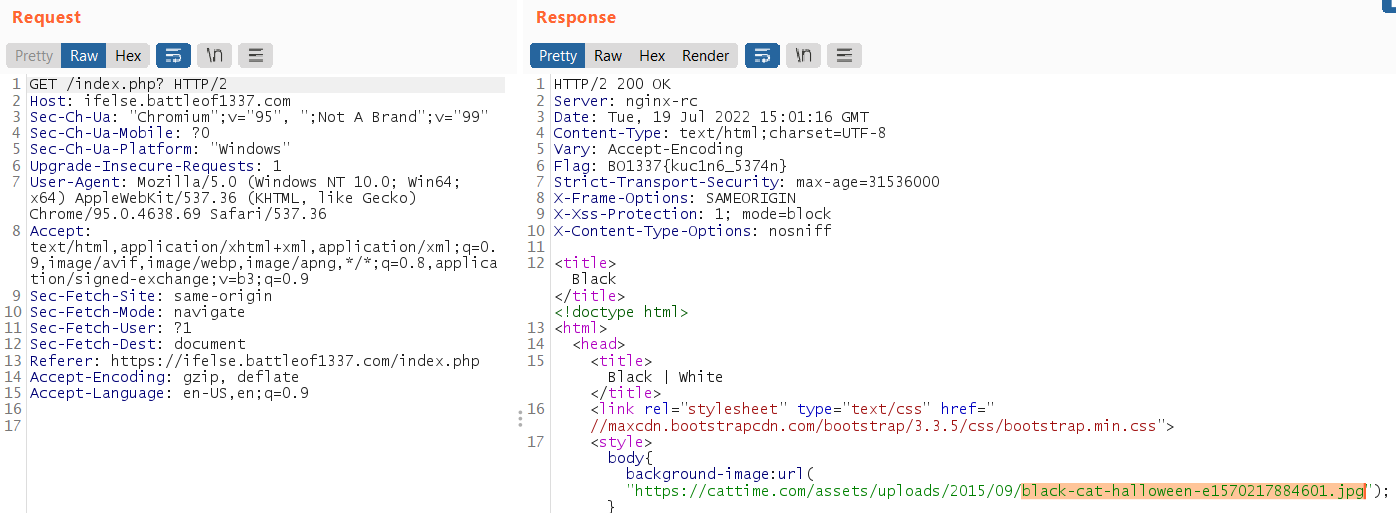
After some experiment, adding flag as parameter will return the flag as the response header!
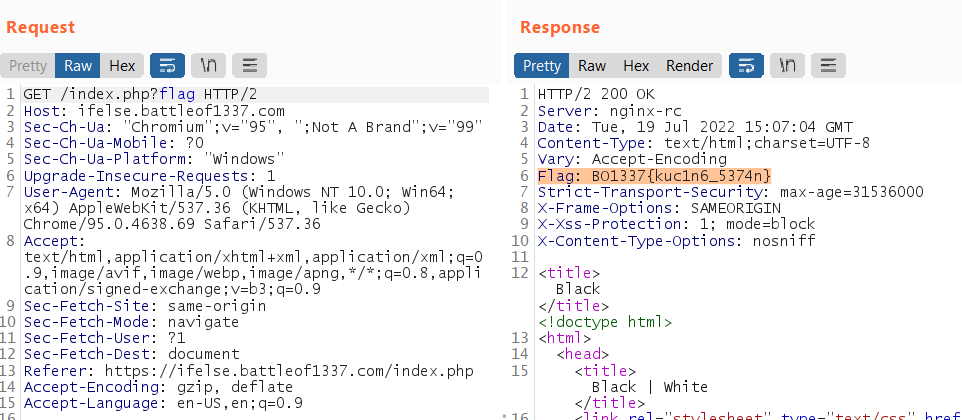
Flag
BO1337{kuc1n6_5374n}
Semerah Padi
Attachment
We are given a Packet Capture (.pcap) file, we can view it with WireShark or we can tcpflow to extract the packets data
tcpflow -r flaghere.pcap
reportfilename: ./report.xml
It extracted two data files:
ls
192.168.000.036.54578-192.168.000.037.31337 192.168.000.037.31337-192.168.000.036.54578 flaghere.pcap report.xml
One file contains a very long text:
GET /Flag HTTP/1.1
User-Agent: Wget/1.21
Accept: */*
Accept-Encoding: identity
Host: 192.168.0.37:31337
Connection: Keep-Alive
HTTP/1.0 200 OK
Server: SimpleHTTP/0.6 Python/3.8.10
Date: Fri, 01 Jul 2022 13:24:52 GMT
Content-type: application/octet-stream
Content-Length: 36399
Last-Modified: Fri, 01 Jul 2022 13:23:17 GMT
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. In vitae turpis massa sed elementum tempus egestas sed. Sed turpis tincidunt id aliquet. Semper feugiat nibh sed pulvinar proin gravida hendrerit. Fermentum posuere urna nec tincidunt praesent semper feugiat nibh. Elit sed vulputate mi sit amet mauris. Eros donec ac odio tempor orci dapibus. Euismod nisi porta lorem mollis aliquam ut. Mauris sit amet massa vitae tortor condimentum lacinia quis vel. Quis ipsum suspendisse ultrices gravida dictum fusce ut placerat.
Tincidunt nunc pulvinar sapien et ligula ullamcorper. Turpis cursus in hac habitasse platea. Nisl rhoncus mattis rhoncus urna neque. Magna etiam tempor orci eu. Commodo sed egestas egestas fringilla phasellus faucibus scelerisque. Lectus urna duis convallis convallis. Proin fermentum leo vel orci porta non pulvinar neque. Quis varius quam quisque id diam vel quam. Cursus metus aliquam eleifend mi in nulla posuere sollicitudin. Proin sagittis nisl rhoncus mattis rhoncus urna neque. Adipiscing commodo elit at imperdiet dui. Bibendum enim facilisis gravida neque convallis a.
...
...
...
Then I noticed something odd in line 76:
Lorem mollis aliquam ut porttitor hts/psei.o/WzUetp:/atbncm5NAv Lectus sit amet est placerat.
This looks SUS, and looks like an URL:
hts/psei.o/WzUetp:/atbncm5NAv
Seems it just split the URL into 2 parts and combine them together, so I wrote a python script to arrange back the URL:
text = "hts/psei.o/WzUe"
text2 ="tp:/atbncm5NAv "
for i in range(len(text)):
print(text[i]+text2[i],end='')
# https://pastebin.com/5WNzAUve
Its a pastebin link! Go to the link it show 2 URL again:
https://ufile.io/bo0cubra
https://ufile.io/g6xqrbl2
One is download link for Semerah Padi.mp3, another one is download link for Semerah Padi.wav
Semerah Padi.mp3 is a normal malay song, but the Semerah Padi.wav sounds very weird
Since is a misc challenge, so it could be steganography!
Then I quickly open it with Sonic Visualiser, add spectrogram:
Then I get the flag! As simple as that!

Flag
BO1337{2878f7b0f8deea26a66d642ebe045620efc43091}
RantaianBlok
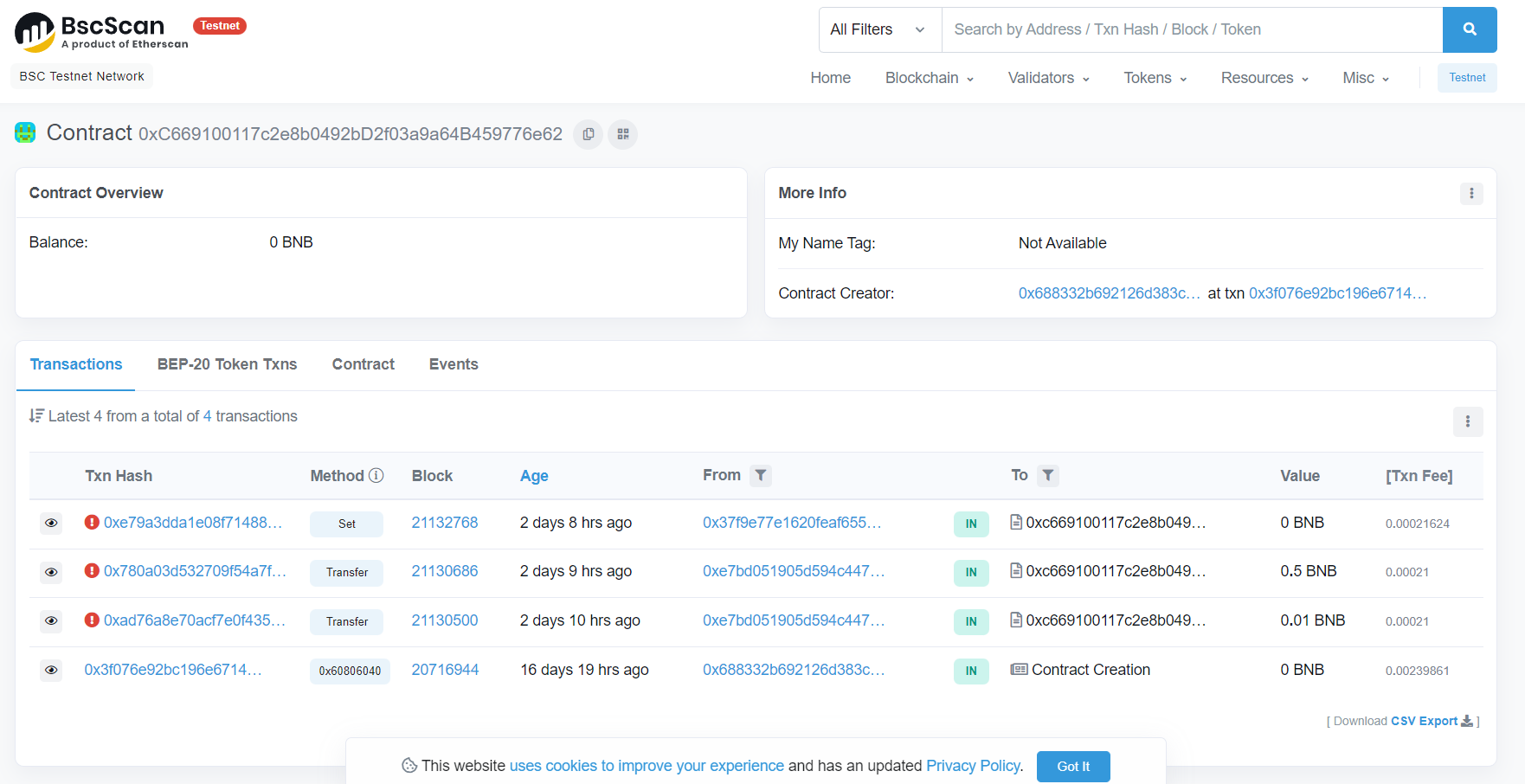
We are given a link to https://testnet.bscscan.com/address/0xc669100117c2e8b0492bd2f03a9a64b459776e62
It seems to related to blockchain? But I have no idea where to find the flag
Then it give a hint:
blockchain.battleof1337.com/abi.txt
The link contains this json data, looks like we need to interact with the smart contract to get the flag!
"abi": [
{
"inputs": [],
"stateMutability": "nonpayable",
"type": "constructor"
},
{
"inputs": [],
"name": "flag",
"outputs": [
{
"internalType": "string",
"name": "",
"type": "string"
}
],
"stateMutability": "view",
"type": "function"
}
],
According to https://www.alchemy.com/overviews/what-is-an-abi-of-a-smart-contract-examples-and-usage
The Application Binary Interface (ABI) of a smart contract gives a contract the ability to communicate and interact with external applications and other smart contracts. Receiving data from external sources can be critical for completing the goals of the application and the user.
I using https://remix.ethereum.org/ to compile the contract and run transactions
First we need to connect our metamask to BSC testnet, because the challenge contract is there
I used this as the contract code and compile it:
contract MyContract{
function flag() public view returns (string memory) {
return "test";
}
}
Choose Injected Provider and put the challenge contract address at the field below:
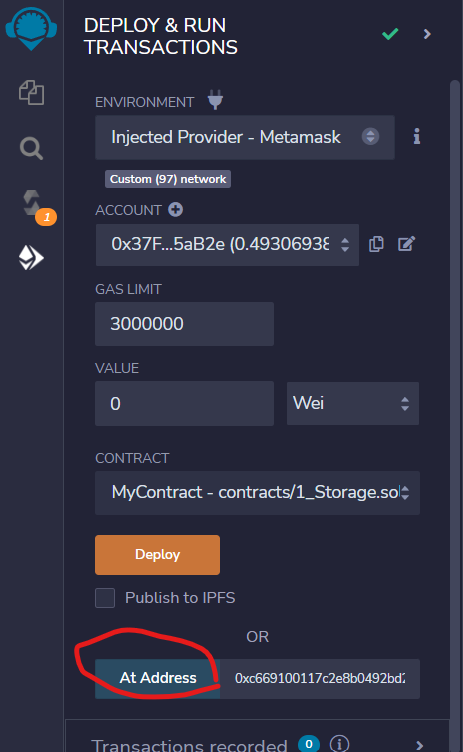
Then click the flag button below, wait and it return the flag!
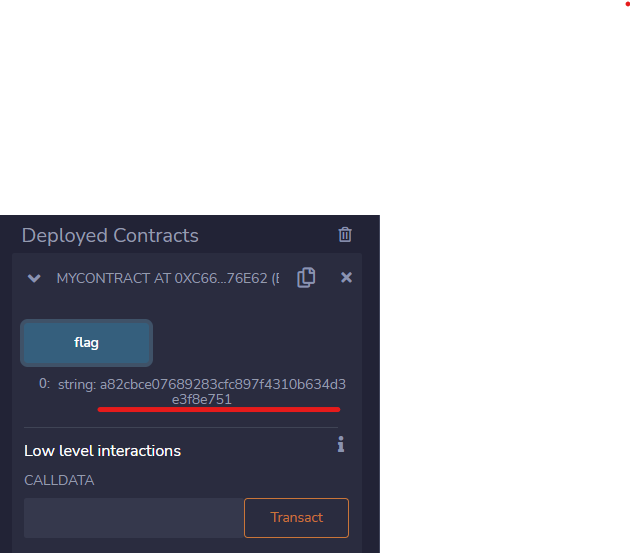
Turns out this is not the flag when I submitted.. after I confirm with the admin seems it return an extra 1 behind
Therefore, the real flag is
BO1337{a82cbce07689283cfc897f4310b634d3e3f8e75}
RedPoint
Attachment:
We are given a PNG file, it just a picture with a red arrow pointing something is the flag

It is in misc category, so steganography again I guess?
Then I used every stegano tools like zsteg, stegsolve etc.. but give me nothing…
After some guessing, then I think maybe the object it pointing is the flag??
I try submit BO1337{screwdriver} as flag and… it worked lol 😑
Probably the most guessy challenge..
Flag
BO1337{screwdriver}
Conclusion
Just know that I’m one of the Top 10! We will playing another round on the final stage! The CTF was great and fun, just some challenges are too guessy. Maybe make put more realistic part for the challenges.